Emails are one of the most common forms of communication in today's world. In fact, many organizations would struggle to function if prevented from emailing customers, vendors, or anyone they often communicate with. Unfortunately, cybercriminals also heavily rely on email in order to steal money or data from your organization. The easiest way to prevent this from happening is by utilizing an email security solution.
What is information security? Click here to read about our Cyber Security 101 Guide!
Are your email servers secure? Learn more about our complimentary security audits. Speak to an email security expert today!
Why is Email Security Important?
With over 91% of cybersecurity attacks beginning from phishing emails, email security has widely become recognized as a crucial part of any IT environment.
Similar to other forms of IT security, email security can help protect confidential company and customer data such as credit card numbers, account information, and more. This helps you maintain your customer's trust, meet compliance standards like HIPAA or PCI DSS, and prevent non-compliance fees.
By utilizing email security in your organization, you can help avoid spam and minimize business risks like ransomware. In fact, the total cost of recovery from a ransomware attack has more than doubled in the past year, from $761,106 in 2020 to $1.85 million in 2021. This form of security is important to deploy to proactively fight against all kinds of email threats.
Read about Phising attacks and how to recognize and avoid them.
Types of Email Security Threats
Email security solutions are built to identify and block a variety of different threats that can land in your inbox. Some of the most common types of email security threats include:
Malware
Malware is malicious software that's sole purpose is to steal data and compromise your computer systems. There are several different types of malware that can be sent through email, but the top three most common types are:
1. Viruses- Viruses are a type of malware that can disrupt your computer system's ability to operate normally. Email viruses are often made of malicious code that is released into a user's computer after interacting with an infected email. Depending on how your organization's IT infrastructure is built, this virus can make its way into your network and compromise more computers or your overall system.
2. Spyware- Spyware is a type of malware that secretly runs in the background of your computer and can grant remote access to cybercriminals. This malware is incredibly dangerous because once spyware is on your computer it can be difficult for your users to identify. By using spyware, cybercriminals gain access to your passwords, personal data, financial information, and more.
3. Ransomware- Ransomware is one of the most common and most costly forms of malware. If your user interacts with an email that contains ransomware, such as clicking a link or opening an attachment, this malware gains access to sensitive information and encrypts it, preventing your organization from accessing it. Then, cybercriminals will demand a ransom for the data to be released back to the organization. It is recommended that you do not pay the ransom if ransomware infects your organization, as cybercriminals are under no obligation to return your data back to you.
Phishing Attacks
According to the FBI, phishing emails were the most common type of cybercrime in 2020, with over 241,324 incidents. These are fraudulent messages that can land in your organization's inbox with the intention of stealing money or confidential information. Often, these can be identified by claims that are too good to be true and the email creates a sense of urgency for the user to click on something or provide personal information. Sometimes users are requested to input passwords into false login screen, asked to fill out personal information, or simply click on a link or attachment to release malware.
Spearphishing
While generic phishing attacks are the most common type of cybercrime, they are often easier to identify as they are generic, automated messages. Spearphishing is similar to phishing attacks but more targeted. These attacks are often more successful as research is done on specific people within an organization to make the messages appear real and believable. This type of social engineering, if done well, can result in huge payouts for cybercriminals while dramatically hurting your organization.
Read about Spearphishing, rising in Office 365 Cloud services.
Business Email Compromise (BEC)
Business email compromise is a more advanced form of spear phishing. This happens when a cybercriminal impersonates an employee, executive, partner, or vendor within an organization to attempt to steal money, confidential information, or distribute malware. For example, a cybercriminal could impersonate a vendor and requests to have their payment information changed. This sounds like a simple and valid request, but can cause great harm to your bottom line.
Spoofing
Spoofing is a technique used in various types of phishing and spearphishing campaigns. With spoofing, a cybercriminal impersonated a legitimate brand in order to earn your trust and access sensitive information. By using logos, similar email structures, and only slightly incorrect URLs, like "netfliix.com" instead of "netflix.com", these emails can look quite convincing. Fortunately, cybercriminals don’t always take the best care in drafting these emails, so sometimes they can be identified through incorrect grammar, poorly written sentences, incorrect spelling, and greetings such as "Hi Dear".
Email Security Key Features
All email security solutions use the same base types of software to protect your inbox. The main features of email security software are spam filters, antivirus protection, data encryption, and image and content control. These, along with other features the solution you choose includes, work together to create a barrier around your inbox, letting only the valid emails through.
Spam Filters
Spam emails, while bothersome, are not inherently malicious. Regardless, spam filters help filter out solicitation and other unnecessary emails, along with malicious emails such as phishing attempts. Spam filters review content within a message to identify false information or spam, as well as blocks emails coming from blacklisted known spammers. If these types of emails don’t end up in your organization's inboxes in the first place, the chance of your users opening malicious content significantly decreases.
Antivirus Protection
Spam filters are a great first line of defense, but antivirus protection is a crucial next step. Similar to the spam filter, antivirus protection scans all incoming and outgoing emails for malicious attachments or other content and blocks them before landing in your or anyone else's inbox. This feature is incredibly important as it can identify and eliminate viruses before they infect your network. This is hugely beneficial as the damage a virus can do to any organization is incredibly detrimental and difficult to recover from.
Data Encryption
Data encryption is the next feature that your email security solution is sure to include. Your organization, like most others, likely shares a great deal of important information via email. If a cybercriminal were to intercept these emails, they would have access to all of the data you just sent or received. By encrypting your email's content and recipient's details during transit, your email security software can prevent hackers from deciphering the data if intercepted. This further protects your organization's and customer's sensitive data from falling into the wrong hands.
Content Filtering
Image and content control is the last main feature in basic email security solutions. Sometimes, when users click on images it can release malware, and large embedded or attached images can negatively impact the email server traffic. Image control prevents these images from being automatically downloaded to help improve server traffic and protect your network. Additionally, it can scan content within emails to prevent emails with inappropriate content, images, and attachments from hitting your employee's inbox.
Click here to see 5 steps to secure your organization's E-Mail.
What to look for in an Email Security Platform?
The features listed above- spam filters, antivirus protection, data encryption, and image and content control- are just the base of any email security solution. When looking for a comprehensive and robust email security solution, it's important to ask the following questions.
1. How advanced are the features?
All email security software has basic security functions to prevent malware, phishing attacks, spam, and viruses. As cybercriminals become more advanced, their attacks become too sophisticated for just these generic security functions. Before settling on an email security solution, know what other types of advanced techniques are included in the software, such as sandboxing, AI or machine learning, or email security training for your staff.
2. How robust is it?
Does your solution include data loss prevention? What features are included in the data encryption? Understanding exactly what additional security features are included in your email security software will help you be aware of how comprehensive of a solution you're looking at.
3. How easy is it?
One crucial part of any security software is ease of use. IT works best when it's in the background and your user's don’t have to think about it. Having one, centralized location where IT staff can set policies and check on reports can improve usability and provide an easy solution to your entire organization.
4. How accurate is it?
With an email security solution, it's possible that emails can be mistakenly blocked from your inbox or that malicious emails make it past the screening. By understanding exactly how accurate your solution is, you can mitigate these false reports and ensure high levels of security and accuracy.
Take a look at 4 reasons why security compliance is important for your organization!
Email Security Solutions Comparison
While there are several different email security solutions you could choose from, here are our top 4 solutions for you to consider
Barracuda Networks Total Email Protection
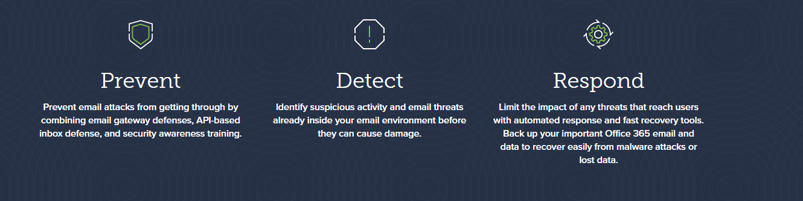
Barracuda Network's Total Email Protection protects against all 13 types of email threats from the least complex, such as spam and malware, to the most complex like conversation hijacking and account takeover. With gateway defense and resiliency, API-based inbox defense, security awareness, and incident response, this solution is one of the most robust and comprehensive ones on the market. Barracuda's Total Email Protection will:
1. Prevent email attacks from getting through email gateway defenses
2. Detech suspicious activity and email threats already inside the environment
3. Respond and limit the impact of threats that reach users.
*Please note that this backup is specifically for Office 365, so Google Workspace users will want to choose a different solution.
SonicWall Hosted Email Security
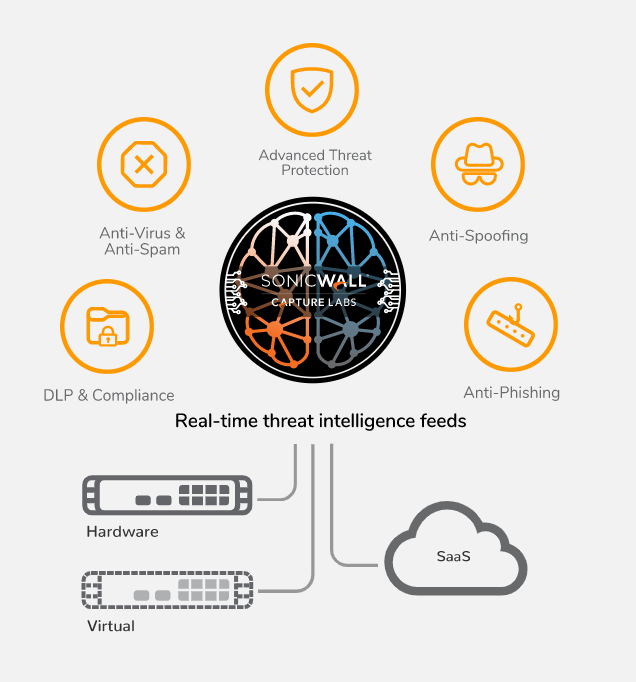
SonicWall's Hosted Email Security is a great email security solution for those who want an on-premises solution. This multilayered solution provides inbound and outbound protection from complex email threats such as zero-day threats and business email compromise. Additionally, this solution includes email data loss prevention to assist in compliance efforts. Deployments are scalable and flexible, and management is simplified. With granulated reports for attachments, URLs, junk mail, and more, your IT staff will always be in the know on all things email security.
Proofpoint Email Security
ProofPoint Email Security claims that they deliver the "most effective unified solution to protect your people and critical data from advanced email threats". With 6 different email security products email protection, targeted attack protection, email fraud defense, threat response auto-poll, internal email defense, and email continuity, it's not hard to see why. Not only can this solution protect against traditional and advanced email threats, it can identify your Very Attacked People (VAP), provide visibility and insights around them, and help mitigate risk.
Mimecast Email Security

This cloud-based email security solution protects your organization and employees from inbound threats. Policy-based information protection solutions are integrated with the email security gateway to enable content control and encryption to protect performance and system availability. Additionally, this solution uses advanced techniques like sandboxing to scan and block malicious attachments within emails.
Conclusion
Email security is a crucial part of your organization's overall security strategy. It can help you stay compliant, keep your confidential information safe, and keep your customer's trust. As cybercriminals become more advanced, the threats become more difficult to identify. That’s why you need to ensure that the email security solution you choose is robust and comprehensive, and has advanced features to keep you safe. Some of our favorite email security solutions are Barracuda Total Email Protection, SonicWall, ProofPoint, and Mimecast, but any solution that meets the same criteria will work well for your organization.
Blog post: The ultimate guide to Endpoint security. Top Endpoint Security Solutions (2021).
Contact us today to see what Email Security solution is right for your organization.



COMMENTS